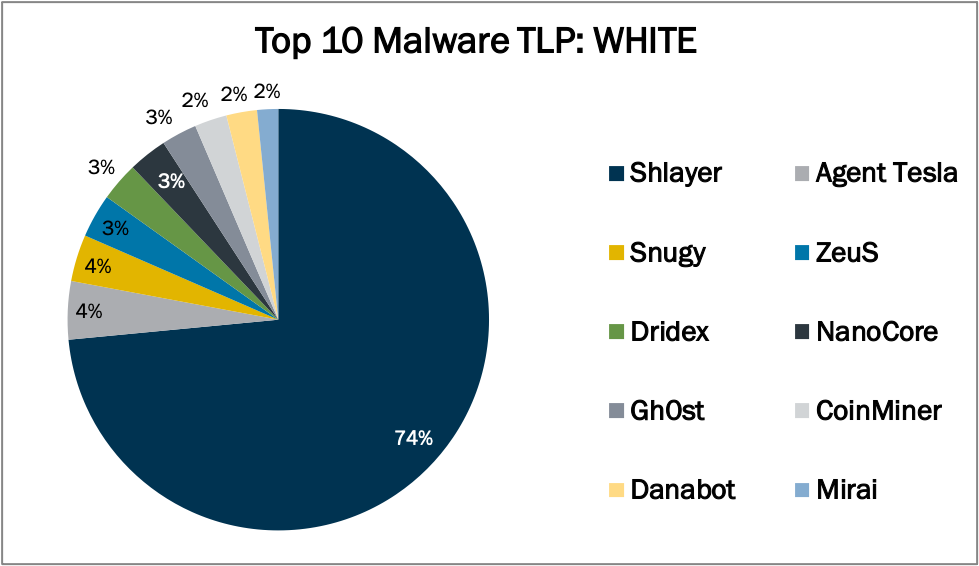
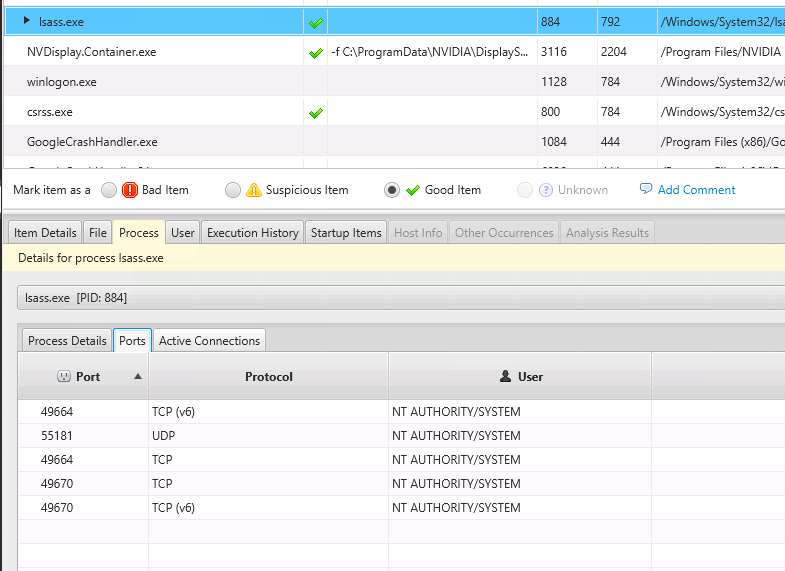
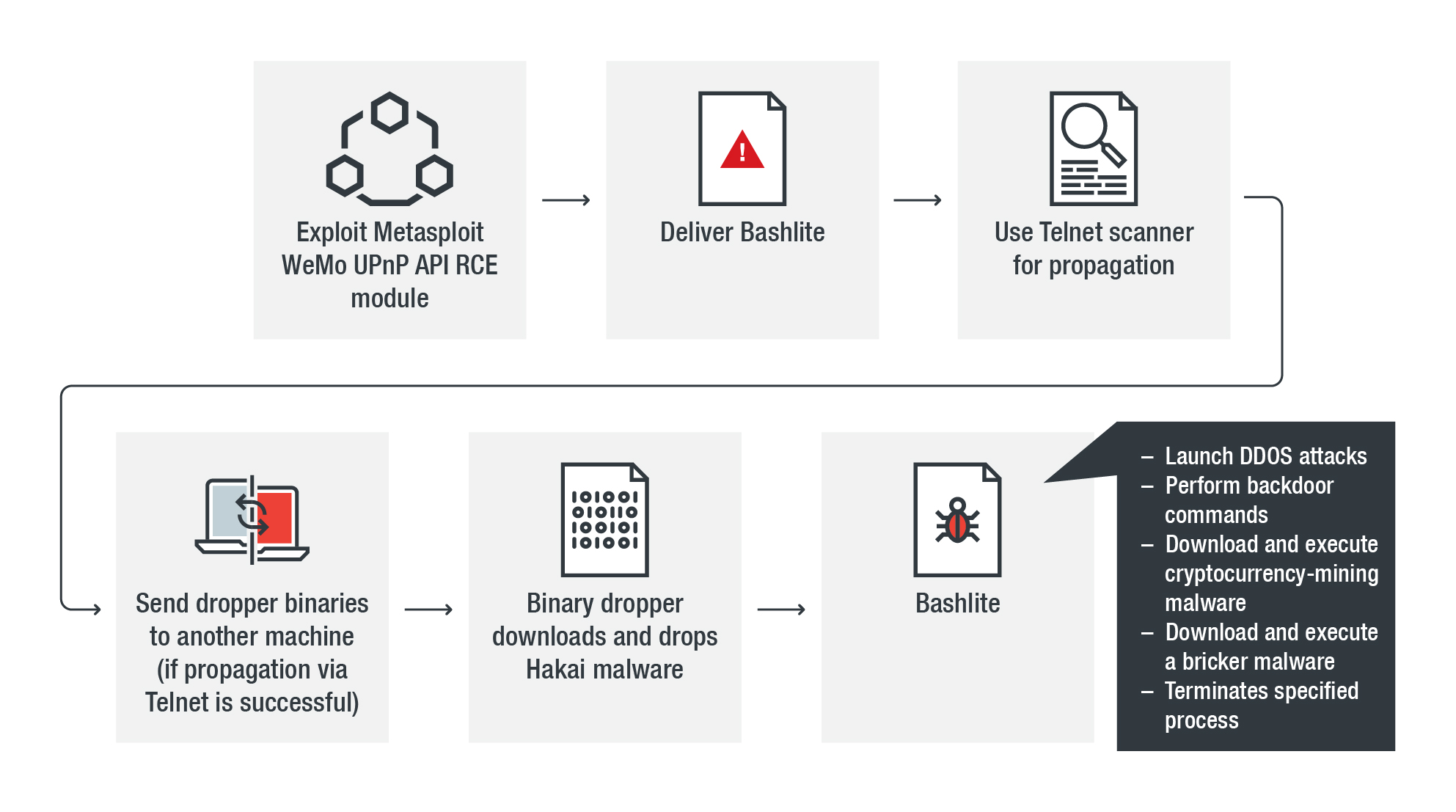
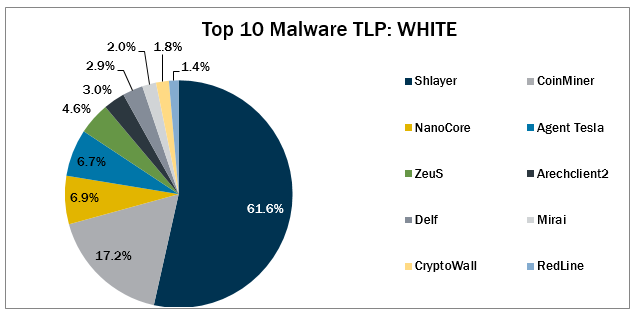
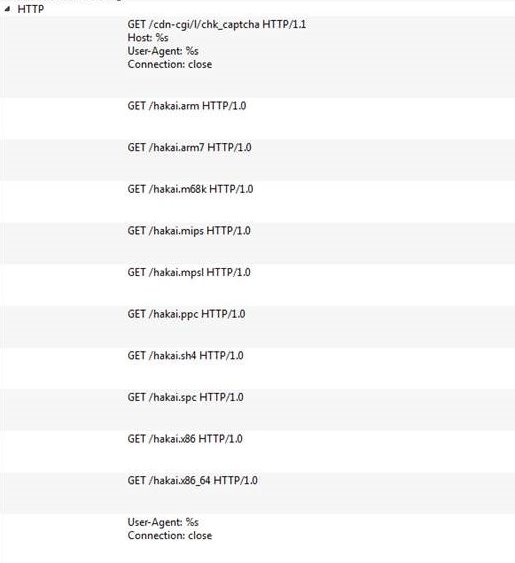
Nextron Systems on Twitter: "We're sharing our YARA rules for the Gopuram malware & related files with the community so that even users of free THOR Lite can detect that malware &

Malware Being Distributed by Disguising Itself as Icon of V3 Lite - Malware Analysis - Malware Analysis, News and Indicators





![How To Remove ALL Viruses From Android [2023 Updated] How To Remove ALL Viruses From Android [2023 Updated]](https://malwaretips.com/blogs/wp-content/uploads/2020/05/Malicious-Apps.jpg)